Cyber Influence and Cognitive Threats: Unveiling the Perils of a Digital Age

Navigating the Labyrinth of Cyber Influence
In the ever-evolving realm of digital technology, the boundaries between our physical and online worlds continue to blur. Amid this technological tapestry, a profound shift is occurring—one that warrants our undivided attention. It is the rise of cyber influence, a clandestine force that operates in the shadows, seeking to shape our thoughts, beliefs, and behaviors.
5 out of 5
| Language | : | English |
| File size | : | 14635 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 229 pages |
Cyber influence manifests in a multitude of forms. From tailored advertisements that subtly nudge us towards specific purchasing decisions to sophisticated deepfake technologies that can manipulate our perception of reality, the tools at its disposal are vast and ever-expanding.
As we navigate this uncharted territory, it becomes imperative to equip ourselves with a discerning eye, capable of discerning the subtle cues and machinations employed by those who seek to sway our minds. The book "Cyber Influence and Cognitive Threats" serves as an invaluable guide, meticulously dissecting the various strategies and tactics used to manipulate our cognitions.
Cognitive Threats: A Looming Shadow in the Digital Landscape
Beyond the overt attempts to influence our behavior lies a more insidious threat: cognitive threats. These threats operate on a subconscious level, exploiting vulnerabilities in our cognitive processes to sow discord, spread misinformation, and undermine our critical thinking abilities.
Cognitive threats can manifest in various forms, including:
- Selective exposure: Tendency to seek out information that aligns with our existing beliefs, leading to a distorted view of reality.
- Confirmation bias: Seeking evidence that supports our preconceived notions, while ignoring or dismissing contradictory information.
- Priming: Exposure to subtle cues that can subconsciously influence our thoughts, feelings, and behaviors.
- False consensus: Assuming that others share our beliefs and opinions, even when there is no evidence to support this assumption.
The book delves into these cognitive threats in detail, providing a framework for understanding their mechanisms and identifying their potential risks. By shedding light on these hidden vulnerabilities, "Cyber Influence and Cognitive Threats" empowers us to safeguard our minds against manipulation and distortion.
Cyber Influence and Cognitive Threats: A Call for Vigilance
As we traverse the treacherous waters of the digital age, the convergence of cyber influence and cognitive threats poses a formidable challenge to our collective psyche. The consequences of unchecked manipulation can be far-reaching, impacting our democracies, social cohesion, and personal well-being.
"Cyber Influence and Cognitive Threats" serves as a clarion call for vigilance, urging us to become more aware of the forces at play and to develop strategies for countering their insidious effects. By fostering a culture of critical thinking, skepticism, and digital literacy, we can create a bulwark against the erosion of our cognitive integrity.
Empowering Ourselves in the Face of Cyber Influence and Cognitive Threats
The realm of cyber influence and cognitive threats is complex and ever-evolving. However, by embracing the insights offered in "Cyber Influence and Cognitive Threats," we can empower ourselves to navigate this treacherous landscape with greater resilience and discernment.
Here are some strategies to combat cyber influence and cognitive threats:
- Cultivate critical thinking skills: Question information, seek diverse perspectives, and evaluate sources before forming opinions.
- Be aware of cognitive biases: Recognize how our preconceptions can influence our judgment and seek out information that challenges our existing beliefs.
- Practice mindfulness: Pay attention to your thoughts and emotions, noticing any external influences that may be shaping them.
- Seek support: Discuss your concerns with trusted friends, family, or professionals who can provide a different perspective.
- Engage in digital hygiene: Limit screen time, unfollow accounts that promote misinformation, and use privacy-enhancing tools to protect your data.
: A Blueprint for Navigating the Digital Maze
"Cyber Influence and Cognitive Threats" is an essential guidebook for navigating the complexities of the digital age. By illuminating the intricate mechanisms of cyber influence and cognitive threats, the book empowers us to safeguard our minds, preserve our critical thinking abilities, and navigate the treacherous waters of the online world with greater resilience and discernment.
As we step into the future, let us embrace the lessons imparted in this groundbreaking work. By embracing critical thinking, fostering skepticism, and cultivating digital literacy, we can create a more informed, resilient, and empowered society that is immune to the insidious threats that seek to manipulate our minds.
5 out of 5
| Language | : | English |
| File size | : | 14635 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 229 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Rosemary Aitken
Rosemary Aitken Jack Albrecht
Jack Albrecht Marina Frolova Walker
Marina Frolova Walker Jason T Newsom
Jason T Newsom Michael D Lyman
Michael D Lyman Barry Moreno
Barry Moreno John E Prussing
John E Prussing Story Clark
Story Clark Jesse H Choper
Jesse H Choper Susan Herrington
Susan Herrington Tony Horwitz
Tony Horwitz C Behan Mccullagh
C Behan Mccullagh Joshua Chen
Joshua Chen Jim Cobb
Jim Cobb Hannibal Travis
Hannibal Travis Ashish Makhija
Ashish Makhija Stephen Jay Gould
Stephen Jay Gould Henry Reichman
Henry Reichman Jim Davidson
Jim Davidson Jim Storhok
Jim Storhok
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!
 Jace MitchellUnveiling Egypt's Architectural Treasures: The Archaeology and History of...
Jace MitchellUnveiling Egypt's Architectural Treasures: The Archaeology and History of...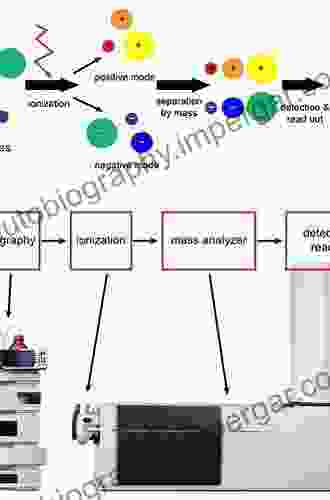
 Joel MitchellMethods For GC-MS and LC-MS: A Comprehensive Guide to Advanced Analytical...
Joel MitchellMethods For GC-MS and LC-MS: A Comprehensive Guide to Advanced Analytical... Jayson PowellFollow ·18.9k
Jayson PowellFollow ·18.9k Roger TurnerFollow ·11.4k
Roger TurnerFollow ·11.4k Mario SimmonsFollow ·19.1k
Mario SimmonsFollow ·19.1k Derek CookFollow ·2.7k
Derek CookFollow ·2.7k Ira CoxFollow ·18.7k
Ira CoxFollow ·18.7k Richard SimmonsFollow ·13.6k
Richard SimmonsFollow ·13.6k Glenn HayesFollow ·14.8k
Glenn HayesFollow ·14.8k Edwin BlairFollow ·16.1k
Edwin BlairFollow ·16.1k

 Phil Foster
Phil FosterBookkeeping Essentials: How to Succeed as a Bookkeeper
Bookkeeping is the process...

 Charles Bukowski
Charles BukowskiUnveiling the Unseen: The Occupiers Experience - A...
In the vibrant tapestry of contemporary...
5 out of 5
| Language | : | English |
| File size | : | 14635 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 229 pages |