Unlocking the Secrets: Navigating the Internet of Things Threats Landscape and Implementing Effective Countermeasures

The Internet of Things (IoT) has revolutionized our lives, connecting countless devices to the internet and enabling unprecedented levels of convenience and automation. However, this interconnectedness also introduces a new set of security challenges. IoT devices are often vulnerable to attacks due to weak security measures, lack of updates, and the transmission of sensitive data over unsecured networks.
5 out of 5
| Language | : | English |
| File size | : | 13079 KB |
| Print length | : | 358 pages |
In this comprehensive guide, we will delve into the intricate threatscape of the IoT, exploring the latest vulnerabilities, attack vectors, and proven countermeasures to safeguard your connected devices. Whether you are a seasoned cybersecurity professional or an individual seeking to protect your IoT ecosystem, this article will provide invaluable insights and practical strategies to mitigate risks and ensure the security of your IoT environment.
Common IoT Threats and Vulnerabilities
Understanding the nature of IoT threats is crucial for developing effective countermeasures. Some of the most common threats include:
1. Device Hijacking
Attackers can gain unauthorized access to IoT devices, taking control of their functionality and using them for malicious purposes such as launching DDoS attacks, spreading malware, or spying on users.

2. Data Breaches
IoT devices often collect and transmit sensitive data, including personal information, location data, and usage patterns. This data can be intercepted by attackers, leading to privacy breaches and identity theft.

3. Malware Infections
Malware designed specifically for IoT devices is becoming increasingly prevalent. These malicious programs can infect devices, disrupting their functionality, stealing data, or creating botnets for DDoS attacks.

4. Network Attacks
IoT devices are often connected to unsecured networks, making them vulnerable to network attacks such as man-in-the-middle attacks, eavesdropping, and denial-of-service attacks.

Effective IoT Countermeasures
To mitigate these threats, it is essential to implement robust countermeasures. Here are some of the most effective strategies:
1. Strong Device Security
Enforce strong security measures on IoT devices by using complex passwords, enabling two-factor authentication, and regularly updating firmware and software.

2. Network Segmentation
Segment IoT devices onto a separate network to limit the risk of attacks spreading to other parts of the network.

3. Data Encryption
Encrypt all sensitive data transmitted to and from IoT devices to prevent interception and data breaches.

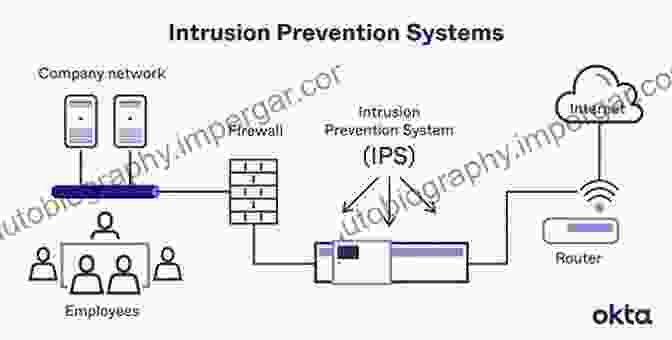
4. Intrusion Detection and Prevention Systems (IDPS)
Deploy IDPSs to monitor network traffic for suspicious activity and prevent malicious attacks.
5. Regular Audits and Assessments
Conduct regular security audits and assessments to identify vulnerabilities and ensure the effectiveness of countermeasures.

Navigating the IoT threats landscape requires a proactive and comprehensive approach. By understanding the common threats, implementing robust countermeasures, and staying vigilant against emerging threats, you can safeguard your connected devices and ensure the security of your IoT ecosystem. Remember, the key to effective IoT security lies in a multi-layered approach that addresses both device and network vulnerabilities.
This guide has provided a comprehensive overview of IoT threats and countermeasures. For further insights and in-depth analysis, I highly recommend the book "Internet of Things Threats Landscape and Countermeasures". This authoritative resource delves into the intricacies of IoT security, providing a roadmap for safeguarding your connected devices in the face of evolving threats.
5 out of 5
| Language | : | English |
| File size | : | 13079 KB |
| Print length | : | 358 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Elaine Taylor Klaus Mcc Cpcc
Elaine Taylor Klaus Mcc Cpcc Shivani Gupta
Shivani Gupta Inge Heyer
Inge Heyer Franz Rosenzweig
Franz Rosenzweig Aini Aman
Aini Aman Anthony Audain
Anthony Audain Steven B Mendelsohn
Steven B Mendelsohn Jenni Schaefer
Jenni Schaefer Teodiano Freire Bastos Filho
Teodiano Freire Bastos Filho George M Taber
George M Taber Gwen Bailey
Gwen Bailey Mary Beth Chapman
Mary Beth Chapman Mark Henderson
Mark Henderson Valiant Thor
Valiant Thor Judith E Glaser
Judith E Glaser Layla Tacy
Layla Tacy Don Mayer
Don Mayer John Nielsen
John Nielsen Nilton Bonder
Nilton Bonder Steve Wiegand
Steve Wiegand
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Elliott CarterUnveiling the Intricacies of Education: Concepts, Schools, and Contemporary...
Elliott CarterUnveiling the Intricacies of Education: Concepts, Schools, and Contemporary...
 Manuel ButlerAlmost Dead Novel: A Chilling Thriller That Will Keep You on the Edge of Your...
Manuel ButlerAlmost Dead Novel: A Chilling Thriller That Will Keep You on the Edge of Your... Logan CoxFollow ·3.7k
Logan CoxFollow ·3.7k Oliver FosterFollow ·3.6k
Oliver FosterFollow ·3.6k Joshua ReedFollow ·8.8k
Joshua ReedFollow ·8.8k Eddie PowellFollow ·17k
Eddie PowellFollow ·17k Fernando PessoaFollow ·11.3k
Fernando PessoaFollow ·11.3k Emanuel BellFollow ·3.9k
Emanuel BellFollow ·3.9k Nathaniel HawthorneFollow ·9.8k
Nathaniel HawthorneFollow ·9.8k Jordan BlairFollow ·11.2k
Jordan BlairFollow ·11.2k

 Phil Foster
Phil FosterBookkeeping Essentials: How to Succeed as a Bookkeeper
Bookkeeping is the process...

 Charles Bukowski
Charles BukowskiUnveiling the Unseen: The Occupiers Experience - A...
In the vibrant tapestry of contemporary...
5 out of 5
| Language | : | English |
| File size | : | 13079 KB |
| Print length | : | 358 pages |